In this investigation, we researched three special military units of the Russian armed forces, known by their numbered names: military unit 74455, military unit 26165, and military unit 29155.
These military units are engaged in information warfare, but they use different methods, sometimes not informational ones at all.
- The military unit 74455 is the command center. The center's military personnel are engaged in cryptography, development and conduct of PSYOP, cyber operations involving hacking and theft of important government documents, interference in the election campaigns of US deputies, and also development and distribution of malware at the level of government agencies.
- The military unit 26165 is involved in the development and conduct of cyberattacks, the creation of malware, including X-Agent, interference in the US election process, and penetration of militaries’ computers, and also into computers of political, governmental and non-governmental organizations.
- The military unit 29155 is involved in "physical operations" that are not typical for intelligence units: the bombing of military warehouses in the Czech Republic in 2014, the attempted poisoning of Bulgarian businessman Gebrev, the attempted murder of the Skripals in Salisbury, other sabotage and physical destruction of persons or objects.
During the investigation, we studied the structure of these military units, the specifics of their work, the specification of tasks and methods of achieving goals. We also gained access to information about some of the Special Forces personnel (40 persons’ data), which we will share with you in the following sections.
Molfar in social networks 👉 Molfar Global
The subordination structure of the special units of the Russian Armed Forces
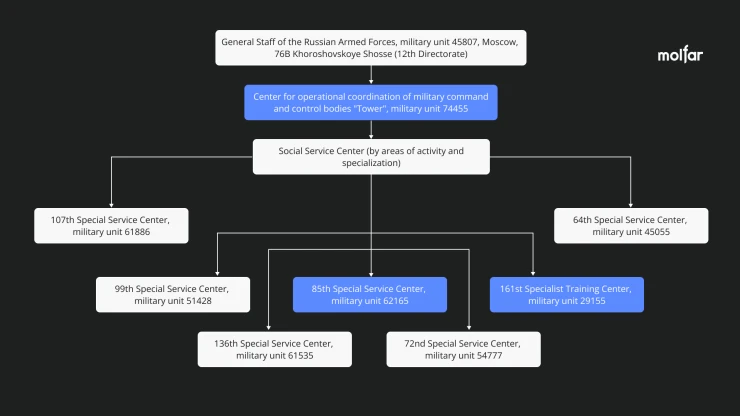
The Main Directorate of the General Staff of the Russian Armed Forces / GRU, through the 12th Directorate, which deals with information warfare, is subordinated to structural units in the Center for Operational Coordination of Military Command and Control.
The military unit 74445 is called "Tower" and it acts as a center for operational coordination of military command and control.
"Tower" is subordinated to the Special Service Center, which includes at least 7 military units in various areas of operation. All of them are special units involved in the assessment, planning and implementation of information and psychological operations. Thus, military units 26165 and 26155 have different specializations, but both are subordinated to the main center "Tower", under the number of military unit 74445.
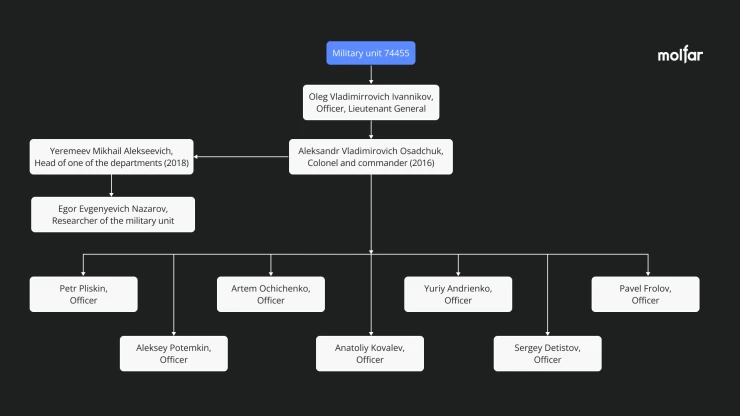
Military unit: 74455
The unofficial name is "Tower". Officially, the military unit's address is the Novator business center, but at the entrance there is a sign with the name "Center for the Management of Daily Activities" – the name of the research institutes created to coordinate the activities of military command and control bodies. The center appears in internal reports as the Fancy Bear hacker group. U.S. intelligence agencies believe that the hacker group, which includes the 74455 and 26165 units, was created in 2004.
The list of military units in Moscow and the region does not include the military unit 74455, and all known physical addresses of the unit are also excluded from the list, except for one – Khoroshivskoye Highway, where four military units with different numbers are located: 45807, 40273, 61535, 77065.
The known address of military unit 74455 is 22 Kirova Street, Moscow region, Khimki, Moscow. However, in the court decision, where the military unit 74455 appears, a different address is indicated: military town №48/1, Svobody Avenue 21/2. The official address is 76 Khoroshivske Highway.
Known activities of the military unit 74455

2018 year: 12 GRU officers have been charged with interference in the 2016 US presidential election and theft of documents as a result of an attack on the internal email of the US Democratic Party. Among the military units named in the indictment are units 74455 and 26165.
2020, the first accusation: 6 officers of the military unit 74455 were charged by the US with attacks on the Olympic Committee and causing $11 billion in damage, of which at least $1 billion was direct damage caused by the US. The same officers were also accused of cyberattacks using the NotPetya virus on Ukrainian energy companies, as well as of intent to obstruct the investigation into the Skripal poisoning in the UK.
2020, the second accusation: In February 2020, the U.S. State Department accused the 74455 military unit of conducting a multi-layered campaign against Georgia.

2020, the third accusation: officers of the military unit 74455 were accused of cyberattacks using the NotPetya virus and Blackout-3 on Ukrainian energy companies, including blackouts in Ivano-Frankivsk region. Ukraine suffered more than other countries from the NotPetya virus: ~10% of government computers, 22 banks, 6 energy companies, 6 hospitals and 2 airports.
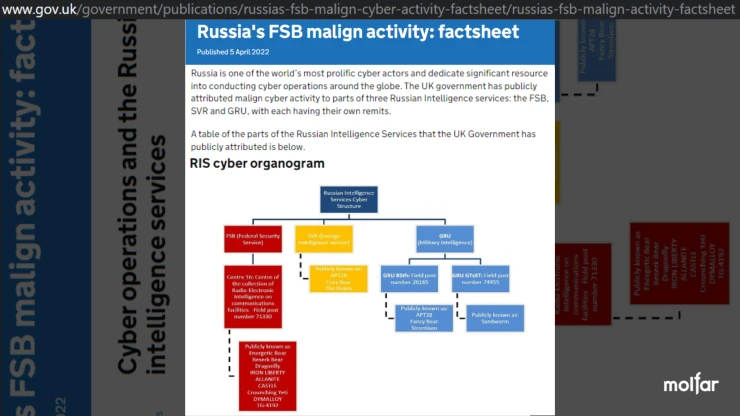
2022 year: In April 2022, Deutsche Welle published information that official London accused the 16th FSB Directorate, military unit 74455 and military unit 26165 of cyberattacks around the world. The publication contains a link to the official UK government gazette.
Additionally:
- in April 2022, the information portal Defence.net published information that the US government is ready to pay a reward of up to $10 million for the location of 6 Russian hackers serving in the military unit 74455 who conducted attacks with the NotPetya virus
- In 2015, the Investigative Committee of the Russian Federation launched an investigation against reserve lieutenant colonel Andrey Nikolenko. In 2015, Nikolenko and his wife Tatyana created a so-called "pyramid scheme" for the resale of iPhones and MacBooks, collected money from the military personnel of the 74455 military unit, which he allegedly invested in the purchase of Apple equipment for further resale at a premium and promised a 10% profit within two months. 17 servicemen and acquaintances of the couple invested from hundreds of thousands to millions of rubles through the Antey company owned by Nikolenko's wife. The company did not conduct any activity. Nikolenko was arrested in 2017 but released in 2018.
Command of the military unit 74445 "Tower"

Aleksandr Vladimirovich Osadchuk (17.11.1962, +79032410466, +79037970357, [email protected], [email protected], passport: 4513023827) – Colonel and Commander in 2016, specialist in information systems. Originally from the city of Obninsk, Kaluga region. In 1985, he graduated from the Kyiv Higher Air Defense Engineering School.
Since September 10, 2021, he has been acting Head of the Main Directorate for Research and Technological Support of Advanced Technologies of the Russian Ministry of Defense. Since November 1, 2021 – Head of the Main Directorate for Innovative Development of the Ministry of Defense of the Russian Federation. He is engaged in the implementation of artificial intelligence technologies in the development of weapons; developments related to the creation of security elements of the national platform based on artificial intelligence.
Known address: 62, Metallurgov Street, Moscow, apartment 155, also: 1, Gorshin Street, Khimki, Moscow Region, apartment 724.
Probable training centers:
- The Military Academy of the Russian Ministry of Defense, unofficially called the "Conservatory," which has a faculty for training officers to work in the 12th Directorate – Information Technology;
- military unit 29155 – 161 training center for training of GRU intelligence specialists.
The known staff and subordination of the military unit 74445 "Tower"
Military unit: 26165
Military unit 26165 is probably the main military unit where Russian hackers serve and work. It is home to the 85th Main Special Service Center, where cryptographers serve.
In 2020, GRU chief Ihor Kostiukov was subject to EU sanctions for a hacker attack on the German parliament. In the past, he was also the commander of the 85th special service center, which is part of the 26165 military unit. Kostyukov is associated with the creation of the hacker groups APT-28 or Fancy Bear, Sofacy Group, Pawn Storm, and Strontium.

In Soviet times, the GRU decryption service, which was engaged in cryptanalysis of intercepted encrypted messages, was located at the address of military unit 26155. Unit 26165 was also mentioned in an investigation by the Russian publication The Insider, where GRU officer Georgy Roshka, who was allegedly involved in hacking French President Emmanuel Macron's email, served.
The ANB identified unit 26165 as the ART28 or Fancy Bear group, which carried out hacker attacks through the Kubernetes cluster using commercial VPN services (CactusVPN, IPVanish, NordVPN, ProtonVPN, Surfshark, and WorldVPN).
The known address of the military unit 26165 is 20 Komsomolsky Lane, Moscow ("Khamovnitsky Barracks").
The known staff and subordination of the military unit 26165
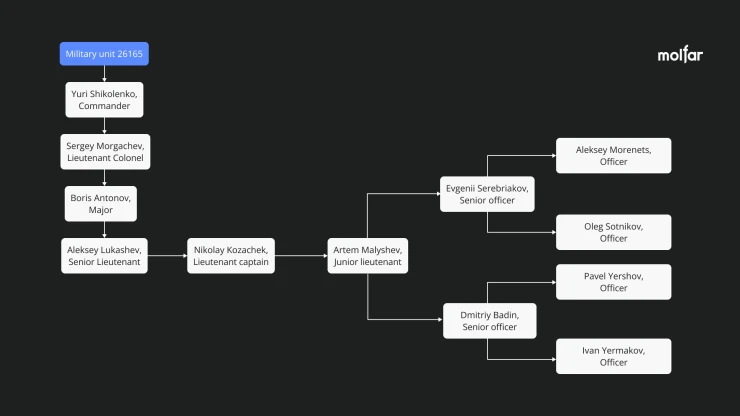
Activities of military unit 26165
According to the US department, this military unit is responsible for the attack on the servers of the Democratic Party and the mail of members of the campaign headquarters of US presidential candidate Hillary Clinton in 2016. The case involves 9 officers of the 26165 military unit and 3 officers of the 74455 military unit.
For these hacker attacks, the GRU paid hackers in bitcoins. The intelligence officers made payments using tokens purchased on an unnamed crypto marketplace. Payments were made for the lease of the dcleaks.com domain and the lease of a server registered to [email protected]. A fadel47 account was created to receive payments in bitcoin.
Command of the military unit 26165
Yuriy Leonidovych Shikolenko (26.04.1979, +79296672304, +79032158814) – Commander of the military unit 26165 as of September 2022. In 2012, he graduated from the Moscow State Technical University "Mirea" (Moscow Institute of Radio Engineering, Electronics and Automation) with a master's degree. As of 2013, he was single. In 2016, he received a doctorate in engineering. In 2022, he participated in the Russian Carbine Shooting Cup. He did not receive a discharge.
Shikolenko owns or had a BMW X5, produced in 2017, VIN Х4ХКТ294600W53078, state number U525ХТ199. Also owns or had a Ford Kuga, produced in 2016, VIN Z6FAHHESMAGC45557, state number A472KN799.
Known address of registration: Moscow region, Krasnoznamensk, Oktyabrskaya Street, 8, apartment 62.
Probable training centers:
- Mozhaisky Military Space Academy – graduated from Morenets in 1999;
- The Military Academy of the Russian Ministry of Defense, unofficially called the "Conservatory," which has a faculty for training officers to work in the 12th Directorate;
- military unit 29155 – 161 training center for training of GRU intelligence specialists.
Military unit: 29155
The military unit is subordinated to the command of the Special Operations Forces, and the SSO headquarters is located in Senezh, north of Moscow. Historically, back in the 1960s, military unit 29155 functioned as a GRU training center. Le Monde wrote in 2019 that the 29155 military unit had a training base in France, in remote mountainous areas such as Chamonix. According to French and British military analysts, the personnel of the military unit 29155 numbered about 20 agents.
The known addresses of the military unit 29155 are: the legal address is 38-A 11th Parkovaya Street, Moscow, and the physical address according to the registers is 4 Mira Street, Orenburg. The address listed in the Bellingcat investigation is the GRU headquarters at Khorosheyevskoye Highway, building 76.
Activities of military unit 29155
The military unit No. 29155 operates using "rough" methods that are not typical for intelligence officers. Among their methods are sabotage and assassination of people abroad, destruction of large objects by explosions.
The experts list the following unsuccessful operations:
- the bombing of military warehouses in Vrbetice, Czech Republic in 2014, the leadership of the sabotage in the Czech Republic is attributed directly to Averyanov;
- 8 GRU officers are suspected of attempting to poison Bulgarian businessman Omelian Gebrev in 2015;
- destabilization of the political situation in Moldova in 2016;
- an attempted pro-Serbian coup in Montenegro in 2016;
- The Spanish Intelligence Service claimed to have identified agents of the military unit 29155 during the rallies for the separation of Catalonia in 2017;
- the attempted poisoning of Sergei Skripal in Salisbury in 2018.
Journalists investigating the cases believe that military unit 29155 is a base for agents specializing in operations in Europe. Chepiga, Sergeyev and Mishkin were identified in the Czech Republic in 2014 and accused of carrying out a sabotage attack on warehouses, killing two people and causing $47 million in damage; they were also spotted in 2016 in Switzerland near the WADA building, trying to steal health data from Western athletes for further publication. They were also identified in the UK in 2016 and accused of attempting to murder Sergei and Yulia Skripal. Sergei Skripal (biography) is a former GRU officer, a colonel, who was arrested in Russia for spying for the UK and later exchanged for captured Russian illegal spies. He received a pardon from Russian President Medvedev and was expelled from Russia. Yulia Skripal is the daughter of Sergei Skripal.
The known staff and subordination of the military unit 29155
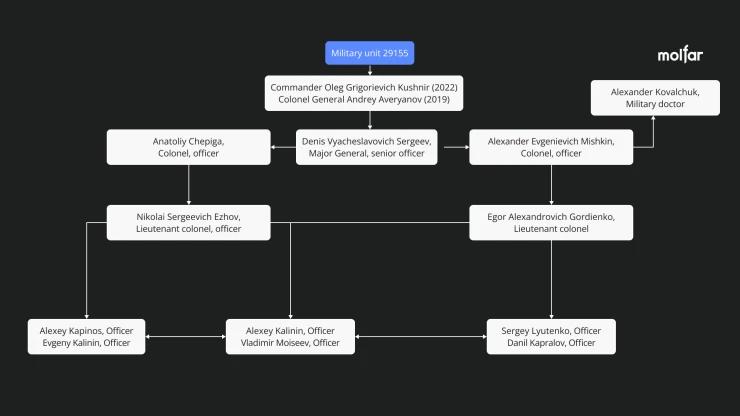
Command of the military unit 29155
Oleg Grigorievich Kushnir (21.01.1985, [email protected], +79258911366, passport: 6304628497) – commander of the military unit 29155 as of September 2022 (1, 2). He was born in Dresden, Germany. Probably studied at the Moscow Higher Combined Arms Command School (MVVKU) and the Combined Arms Academy of the Russian Armed Forces (OAVS).
Relatives:
- Kushnir Madina Alievna (probably the wife, 25.07.1985, VK, [email protected], +79258916477, ads on Avito);
- Kushnir Evgeniya Ivanovna (probably, the mother, 29.01.1961), has children.
Known addresses: St. Petersburg, Neskornykh Avenue, 2, building A, apartment 452, 440; St. Petersburg, Khlopin Street, 9, apartment 3 (wife's address for 2021); Moscow, 190 Glovacheva Street (Moscow Military Commissariat).
The former commander's connection with agents
Anatoliy Chepiga, the former commander of Averyanov's unit, as well as Anatoliy Chepiga, known as "Ruslan Boshirov," were present in the photos and videos of Averyanov's daughter's wedding. The wedding itself took place in one of the restaurants in the village of Senezh, where the SSO headquarters is located. Alexander Mishkin was also supposed to be among the guests, but he was not found in the wedding photos.


Probable training centers:
- The military unit 29155 itself is probably the 161st training center for the training of GRU intelligence specialists;
- Kirov Military Medical Academy (graduated Mishkin);
- Also, it is likely that the soldiers of the military unit 29155 are officers of the SSO, which is selectively enrolled from the Ryazan Guards Higher Airborne Command School, Novosibirsk Higher Military Command School, and the Military Academy of Air Defense of the Russian Federation, named after Marshal of the Soviet Union A.M. Vasilevsky.
Additional locations: military unit 74455, military unit 26165, military unit 29155
To identify additional locations, we analyzed the movement of people allegedly associated with military units between 2020 and 2022.
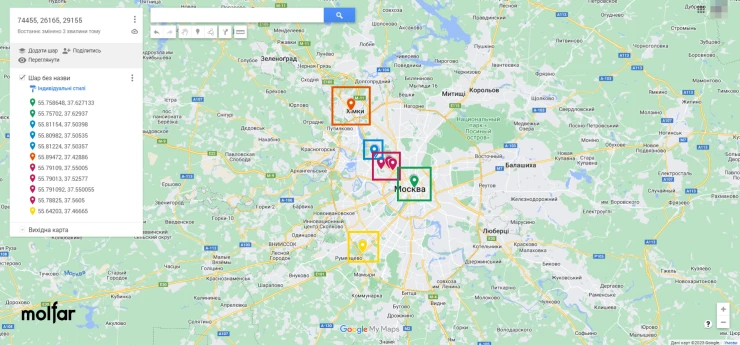
For further analysis, it was assumed that individuals found at one address could have also visited other searched addresses, so the number of search results was narrowed to the number of individuals who were near more than one known address. Based on the list, the coordinates of locations were found that were repeated by different individuals, and among which there may be additional locations of the military unit.
- 55.758648, 37.627133 | 55.75702, 37.62937. Lubyanka Square, close to the buildings of the Federal Security Service of the Russian Federation, the Presidential Administration, the Chamber of Commerce and Industry, and the State Legal Department of the President of the Russian Federation.
- 55.81154, 37.50398 | 55.80982, 37.50535 | 55.81224, 37.50357. Leningrad highway, Sokol district, near the military unit 6796 (33rd special forces detachment "Peresvit").
- 55.89472, 37.42886. Leningrad highway, Khimki district, nearby are (1, 2) buildings behind a barbed wire fence, probably belonging to the rocket and space industry organization NGO Lavochkin.
- 55.79109, 37.55005 | 55.79013, 37.52577 | 55.791092, 37.550055 | 55.78825, 37.5605. In the running area, nearby are (1, 2) buildings behind a barbed wire fence – probably repair and maintenance shops for electric motors and power equipment that belonged to the Znamya machine-building plant.
- 55.64203, 37.46665. Teplostansky Proezd, near the FSB Institute of Criminalistics.
Personal data of special forces military personnel: military units 74455, 26165, 29155
👉 Military unit №74455
1️⃣ Oleg Vladimirrovich Ivannikov (02.04.1967): Officer, Lieutenant General
According to the Bellingcat investigation, he was involved in the delivery of the BUK system to Ukraine, which was used to shoot down the Malaysian MH17 flight. Call sign "Orion". In 2014, he headed the Wagner PMC in Donbas. Biography. In 2004, during the conflict in South Ossetia, he was known as "Andrei Ivanovich Laptev", was the chairman of the Security Council of South Ossetia, and then the head of the Ministry of Defense of South Ossetia.
Contacts: +79266877700, [email protected], Livejournal
Passport: 4511593115. Known address: 60, Akademika Anokhina St., Moscow, apartment 197. Known address: 51a Oktyabrskaya St., Moscow, 398002, Russia.
2️⃣ Aleksandr Vladimirovich Osadchuk (17.11.1962): Colonel and commander
The military unit helped to make stolen documents public through fictional characters DCLeaks and Guccifer 2.0, posted compromising content about Clinton. In the indictment of 2016, he is listed as the commanding officer of the military unit 74455.
Contacts: +79032410466, +79037970357, [email protected], [email protected].
Passport: 4513023827. Known address: 62, Metallurgov str., Moscow, apartment 155, also: Moscow region, Khimki, Gorshina Street, building 1, apartment 724. Related person: Tatiana Borisovna Mikhailova (21.05.1979).
3️⃣ Yeremeev Mikhail Alekseevich (06.09.1969): Head of one of the departments
He was the head of the department in the military unit 74455 in 2018. Professor of the Faculty of Special Information Technologies of the Air Force Academy, co-author of books on cryptography and author of scientific papers on encryption algorithms.
Contacts: +79119878819, [email protected].
Passport: 4014093376, TIN: 781423602946. Known address: 39, Serdobolskaya St., St. Petersburg, apartment 8.
4️⃣ Egor Evgenyevich Nazarov (01.11.1989): Researcher of the military unit
Author of scientific papers in the field of radio communications (1, 2), formerly an associate professor of the Department of Radio Electronics at the Military Training and Research Center of the Air Force "Zhukovsky and Gagarin Air Force Academy".
Contacts: +79162777951, е[email protected], [email protected], [email protected].
Passport: 2010263107. When registering, he indicated the addresses of the military unit: 21/2 Svobody Street and Kirova Street in Khimki.
5️⃣ Aleksey Aleksandrovich Potemkin (20.03.1983): Officer
He headed a unit responsible for managing the information infrastructure used in cyber operations. The infrastructure and social media accounts managed by Potemkin's organization, along with other tools, were used to publish stolen documents through DCLeaks and Guccifer 2.0. From Potemkin's accounts, fake Facebook accounts were registered under the fictitious names of Alice Donovan, Jason Scott, Richard Gingrey and others, which promoted information from the DCLeaks website. He also created the @dcleaks account on Twitter, which promoted the site's materials. The same computer also registered the @BaltimoreIsWhr account, which called for joining a flash mob against Clinton and posting photos with the hashtag #BlacksAgainstHillary.
Contacts: +79660538333, TG: @alexey402, [email protected], [email protected]
Passport: 3804219243, TIN: 461001389084. He indicates the address of the GRU General Staff: 76 B Khoroshevskoye Shosse, the probable address is 426052, Udmurt Republic, Izhevsk, Vechernyaya St., 1, apartment 18. Wife: Potemkina Natalia Stanislavivna (25.03.1987) - 79266721014, [email protected], VK. Probably has a son, Mikhail.
6️⃣ Anatoliy Sergeyevich Kovalev (02.08.1991): Officer
He is mentioned in connection with Osadchuk: "Defendants Osadchuk and Kovalyov were GRU officers who knowingly and intentionally conspired with each other and others to hack into the computers of U.S. citizens and organizations responsible for organizing the 2016 election." In June 2016, Kovalyov, along with other defendants, studied the domains of state election organizations and searched for vulnerabilities on the relevant websites. Kovalev and the others also searched for email addresses of the state's political party members.
Contacts: +79150556650, [email protected], VK.
Passport: 1511951536, TIN:322800244201. He indicates the address of the military unit: 21/2 Svobody Street, military unit.
7️⃣ Yuriy Sergeyevich Andienko (30.05.1988): Officer
He was accused of cyber-attacks using the NotPetya virus on Ukrainian energy companies, with the intention of interfering with the investigation of the Skripal poisoning case in the UK. The United States was also accused of trying to harm the Olympic Games and causing $11 billion in damages, of which at least $1 billion was direct damage to the United States. Photo.
Contacts: +79250784526, [email protected], [email protected], VK, that is linked to an e-mail.
Passport: 4608230478, TIN: 504506704482. Known address: Moscow region, Stupinsky district, Meshcherino village, Meshcherino-1, 12, 23, when registering, he indicated the address of the GRU General Staff: 76 B Khoroshevskoye Shosse, as well as his actual address: Moscow region, Lobnya, 14 A Krupskaya St., apartment 18.
8️⃣ Sergey Vladimirovich Detistov (21.07.1985): Officer
He was accused of cyber-attacks using the NotPetya virus on Ukrainian energy companies, with the intention of interfering with the investigation of the Skripal poisoning case in the UK. The United States was also accused of trying to harm the Olympic Games and causing $11 billion in damages, of which at least $1 billion was direct damage to the United States. Photo.
Contacts: 79165745468, [email protected], [email protected], [email protected], [email protected], VK, OK.
Passport: 6001706476. Known address: 344010, Rostov-on-Don, Mechnikova St., 146A, apartment 52.
9️⃣ Pavel Vladimirovich Frolov (07.06.1992): Officer
He was accused of cyber-attacks using the NotPetya virus on Ukrainian energy companies, with the intention of interfering with the investigation of the Skripal poisoning case in the UK. The United States was also accused of trying to harm the Olympic Games and causing $11 billion in damages, of which at least $1 billion was direct damage to the United States. Photo.
Contacts: [email protected], Skype: live:han-92_2, +79105984581, VK, VK1 – linked to a phone number.
He indicated his registration address as 21/2 Svobody St., post office, another known address: 11871 Proletarskaya St., Kaluga.
1️⃣0️⃣ Artem Valeryovich Ochichenko (08.11.1992): Officer
He was accused of cyber-attacks using the NotPetya virus on Ukrainian energy companies, with the intention of interfering with the investigation of the Skripal poisoning case in the UK. The United States was also accused of trying to harm the Olympic Games and causing $11 billion in damages, of which at least $1 billion was direct damage to the United States. Photo.
Contacts: +79778814491, [email protected], [email protected].
Passport: 4518280242. Known address: Moscow region, Odintsovo district, Sosnovka village, 8, apartment 2.
1️⃣1️⃣ Petr Nikolayevich Pliskin (26.08.1988): Officer
He was accused of cyber-attacks using the NotPetya virus on Ukrainian energy companies, with the intention of interfering with the investigation of the Skripal poisoning case in the UK. The United States was also accused of trying to harm the Olympic Games and causing $11 billion in damages, of which at least $1 billion was direct damage to the United States. Photo.
Contacts: +79164357059, [email protected]
Passport: 0808773870. He indicated the address of his registration – 21/2 Svobody Street, office block.
👉 Military unit №26165
1️⃣ Yuri Leonidovich Shikolenko (26.04.1979): Commander
Unit commander as of September 2022.
Contacts: +79296672304, +79032158814.
Known address of residence: Krasnoznamensk, Moscow region, 8 Oktyabrskaya St., apartment 62.
2️⃣ Viktor Borisovich Netyksho (08.09.1966): Colonel
Commander of military unit No. 26165. According to SPARK, he headed this military unit until January 2018.
Contacts: +79169348027, +79776442784
Known address: 117463 77 Moscow Karamzina proezd 1 k.3 sq.422. Probably wife Oksana Serhiivna Netyksho (20.05.1969) – [email protected], +79150160345.
3️⃣ Dmitry Alexandrovich Mikhailov (26.09.1962): Lieutenant Colonel
Previous unit commander (2018-2022).
Contacts: +79166090528, +79167566121.
Indicated the address of registration near the GRU General Staff, 72 Khoroshevskoye Highway.
4️⃣ Sergey Aleksandrovich Morgachev (22.05.1977): Lieutenant Colonel
He was in command of a unit that developed malware, including X-Agent (previously known as the Fancy Bear hacker group). During the hacking of the networks of the Democratic Congressional Campaign Committee and the Democratic National Committee, Morgachev supervised the accomplices of the criminal scheme who developed and managed the X-Agent program, which was installed on Democratic computers. Place of birth: Kyiv, Ukraine.
Contacts: +79295518624, [email protected].
Passport: 4616338429, TIN: 505016492079. Known address: 103, Vatutina St., building 49, apartment 49, Shchelkovsky district, Moscow region, 141181. Yekaterina Viktorovna Morgacheva is probably the wife.
5️⃣ Boris Alekseyevich Antonov (19.12.1980): Major
He served in the military unit No. 26165. According to the investigation, he headed a unit within the military unit that was engaged in hacking into the computers of military, political, governmental and non-governmental organizations. Around 2016, Antonov led other co-conspirators in a criminal scheme that hacked into the computers of the Democratic Congressional Campaign Committee, the Democratic National Committee, and individuals associated with Hillary Clinton's campaign.
Contacts: +79265594226, skype: zerbob80.
Known address for 2016: Krasnoznamensk, Moscow Region, 2 Oktyabrskaya St., apartment 31.
6️⃣ Aleksey Viktorovich Lukashev (07.11.1990): Senior Lieutenant
Under various virtual names, he sent phishing emails to members of the Clinton campaign and its associates, including the chief of staff. The website dcleaks.com, which published the stolen emails, was registered from the account [email protected], which belonged to Lukashev's account john356gh. On March 19, 2016, Lukashev, using the login John356gh, sent the Chief of Staff an email disguised as a regular Google message asking him to change his password to a more secure one. The link led to a website created by the GRU. The email was sent from the [email protected] mailbox. Lukashev gained access to the desired mailbox the same day. On April 6, 2016, Lukashev created another email account, which differed by one letter from the real email of one of the members of the staff (the document does not specify his name) and sent an email to the staff members with the attached file hillary-clinton-favorable-rating.xlsx (the link also led to a website created by the GRU). He used the nicknames Dan Katenberg and Yuliana Martynova.
Contacts: +79164991216, +79675354117, [email protected].
Known address: St. Petersburg, Shushary settlement, 14 Polotskaya St., apartment 112.
7️⃣ Nikolay Yuryevich Kozachek (29.07.1989): Lieutenant captain, worked in Morgachev's unit
Used different nicknames, developed and managed X-Agent malware. Used the nicknames kazak and blablabla1234565
Contacts: 79014224179, 79684564887, [email protected].
Known address: 53, Ozerkova St., Petergof, apartment 63.
8️⃣ Artem Andreyevich Malyshev (02.02.1988): Junior lieutenant, worked in Morgachev's unit
In or around 2016, he observed the X-Agent malware infiltrating the servers of the Democratic Congressional Campaign Committee and the Democratic National Committee.
Probably: TIN: 772300421938. Known address for 2017: 27, 1 Perervinsky Boulevard, Moscow, 162.
9️⃣ Dmitriy Sergeyevich Badin (15.11.1990): Antonov's aide, senior officer
He controlled the accomplices in the criminal scheme that hacked into the Democrats' computers.
His known address in 2015 was 71 Tamchishina Street, Kursk.
1️⃣0️⃣ Evgenii Serebriakov (26.07.1981): Senior GRU officer
Together with Morenz and two other members of the group, he was expelled from the Netherlands on suspicion of attempting to attack the MH17 court. He is on the EU sanctions list.
Contacts: +79629637937.
Passport: 3802614492, TIN: 463222140814. Known address: Moscow, Kashenkin Lug, 6, bldg. 2, apartment 72. Probably his wife is Oksana Viktorovna Serebryakova ([email protected], skype: aksi_oksana, aksiniushka777, VK).
1️⃣1️⃣ Aleksey Sergeevich Morenets (31.07.1977): Officer
According to Project, Oleksiy Morenets graduated from the Mozhaisky Military Space Academy. Mozhaisky Military Space Academy. In 1999, he graduated (1, 2) from the Faculty of Special Information Technologies. The profile is posted on the FBI website in the Most wanted section. He is accused of cyberattacks on international anti-doping agencies and officials. Along with Sotnikov and two GRU cover officers, he was expelled from the Netherlands on suspicion of trying to attack the MH17 trial. The same group was subject to EU sanctions.
Contacts: +79035444825, TG: @Rae2xiev.
1️⃣2️⃣ Oleg Mikhaylovich Sotnikov (24.08.1972): Officer
Together with Morenets and two GRU cover officers, he was expelled from the Netherlands on suspicion of attempting to attack the MH17 court. He is on the EU sanctions list.
Contacts: +79299715940, [email protected].
Passport: 4617725623. Known address: 10, Podmoskovny Boulevard, Moscow Region, 143401, Krasnogorsk, Moscow Region, apartment 211
1️⃣3️⃣ Pavel Vyacheslavovich Yershov (14.12.1990): Employee of Morgachev's unit
He worked in Morgachev's unit. In 2016 or close to it, he assisted Kozachko and other defendants in testing and finalizing the X-Agent malware before its direct implementation and use.
Possible contacts: +79214223350, VK, ІПН: 695006053516.
1️⃣4️⃣ Ivan Sergeyevich Yermakov (10.04.1986): Antonov's unit, officer
He worked in Antonov's unit. Since about 2010, he has been conducting hacking operations under various virtual names. Around March 2016, he was involved in hacking at least two email accounts, and the information about the election campaign contained there was published on the DCLeaks website. He also gained access to the computer systems of the Democratic Congressional Campaign Committee and the Democratic National Committee, which allowed the attackers to track the actions of Clinton's staff and steal their passwords. He has a sole proprietorship with the KVED "Computer software development".
Contacts: +79167900085, [email protected].
TIN (1, 2): 740502538661. Known addresses: Moscow Region, Krasnogorsk, Otradnoe village, 16 Lisovaya St., apartment 149.
👉 Military unit №29155
1️⃣ Oleg Grigorievich Kushnir (21.01.1985): Commander
Commander of a military unit as of September 2022.
Contacts: +79258911366, [email protected]
Passport: 6304628497. Probably his wife is Madina Kushnir (25.07.1985, [email protected], +79258916477, VK, Skype: kushnir02).
2️⃣ Andrey Vladimirovich Averyanov (29.09.1967): Colonel General, former commander of a military unit
He led the bombings of military warehouses in the Czech Republic in 2014, tried to poison the Bulgarian businessman Gebrev, etc. Pseudonym "Andrey Overyanov". Former head of a military unit, probably 2013-2019.
Contacts: +79269889891, +74997289055.
TIN: 773378888007. Known address: Moscow, 9 Sitlogorskiy lane, apartment 120.
3️⃣ Denis Vyacheslavovich Sergeev (17.09.1973): Major General, senior officer
Participated in the attempted murder of the Skripals in Salisbury, the bombing of military warehouses in the Czech Republic in 2014, the attempted poisoning of Bulgarian businessman Gebrev, etc. His pseudonym is "Sergei Fedotov".
Passport: 0399292244, TIN: 774348990502. His known address is 50 Narodnogo Opolcheniya St., Moscow, apartment 79. Wife – Sergeyeva Tatiana Ivanovna (21.05.1971) – +79164995187, [email protected].
4️⃣ Alexander Evgenievich Mishkin (13.07.1979): Colonel, officer, military doctor
He took part in the attempted murder of the Skripals in Salisbury, the bombing of military warehouses in the Czech Republic in 2014, the attempted poisoning of Bulgarian businessman Gebrev, etc. The pseudonym "Alexander Petrov", in the Czech Republic in 2014 he showed a passport in the name of "Nicolai Popa", a citizen of Moldova.
Contacts: +78125427996.
Passport: 4001912025. Known address: St. Petersburg, Akademika Lebedeva St., 12, lit. A, bldg. 30. Registered address: Moscow, Sumskoy proezd 8, building 2, apartment 78, also at the address of the GRU General Staff – 76 B Khoroshevskoye Shosse.
5️⃣ Anatoly Vladimirovich Chepiga (05.04.1979): Colonel, officer
He took part in the attempted murder of the Skripals in Salisbury, the bombing of military warehouses in the Czech Republic in 2014, the attempted poisoning of Bulgarian businessman Gebrev, etc. The pseudonym "Ruslav Boshirov", in the Czech Republic in 2014 he showed a passport in the name of "Ruslan Tabarov", a citizen of Tajikistan. Biography.
Contacts: +79637167227.
Passport: 0804123252, TIN: 272116050646. His wife is Halyna Viktorivna Chepiga (born on October 1, 1982).
6️⃣ Nikolai Sergeevich Ezhov (01.01.1978): Lieutenant colonel, officer
He participated in the preparation of a sabotage in the Czech Republic in 2014, as well as in the attempted murder of Yemelyan Gerbrev. Pseudonym "Nikolai Kononikhin".
Contacts: +79166223606, [email protected].
Passport: 4702485864. He indicates the address of the GRU General Staff: 76 B Khoroshevskoye Shosse and his residential address: 57 Angarskaya St., building 1, apartment 179, Moscow. His wife is Ksenia Yezhova.
7️⃣ Egor Alexandrovich Gordienko (02.02.1979): Lieutenant colonel, officer, diplomat
Together with Sergeev, he was preparing an operation to assassinate Bulgarian businessman Gebrev in Switzerland. Pseudonym "Georgy Gorshkov". Photo. 2017-2018 – Third Secretary of the Embassy of the Russian Federation, accredited member of the Russian mission to the WTO. In 2018, he left Switzerland in the threat of being discovered.
Contacts: +79175408357, [email protected].
Passport: 6103841971, Passport: 4501747035, TIN: 772704538988. Known address: 34, Perekopskaya St., building 4, apartment 92, Moscow, Russia. Gordienko Olga Vladimirovna is probably the wife.
8️⃣ Alexander Kovalchuk: Military doctor
He was a member of the group that prepared the Skripals' poisoning, together with Chepiga and Mishkin.
9️⃣ Sergey Viktorovich Lyutenko (09.12.1981): Officer
Together with Sergeev and Gordienko, he was preparing an operation to assassinate Bulgarian businessman Gebrev in Switzerland. His pseudonym is "Sergei Pavlov".
Contacts: +79152323209.
He registered the address of the GRU General Staff: 76 B Khoroshevskoye Shosse. Yevheniia Ihorivna Liutenko (24.04.1984) – probably his wife.
1️⃣0️⃣ Ivan Terentiev: Officer
Participated in the attempted murder of Yemelyan Herbrev. Pseudonym "Ivan Lebedev".
1️⃣1️⃣ Alexey Kalinin: Officer
Participated in the attempted murder of Yemelyan Herbrev. Pseudonym "Alexey Nikitin".
1️⃣2️⃣ Vladimir Moiseev: Officer
Participated in the attempted murder of Yemelyan Herbrev. He is also accused of participating in a failed coup d'état in Montenegro.
1️⃣3️⃣ Danil Vladimirovich Kapralov (23.03.1983): Officer
Participated in the attempted murder of Yemelyan Herbrev. Pseudonym "Daniil Stepanov". In 2019, his place of work is the Ministry of Foreign Affairs of the Russian Federation.
Contacts: +79105645969, +79057908614.
Passport: 4515399247, TIN: 660310235367. He indicates the address of the GRU General Staff: 76 B Khoroshevskoye Shosse. Wife – Kapralova Olha Mykolaivna (31.01.1986). Daughter – Kapralova Varvara Danilovna (25.03.2010).
1️⃣4️⃣ Alexey Kapinos: Officer
He participated in the preparation of a sabotage in the Czech Republic in 2014.
1️⃣5️⃣ Evgeny Kalinin: Officer
He participated in the preparation of a sabotage in the Czech Republic in 2014.
✉️ To contact the team and receive a comment, please fill out the form below or send your request to: [email protected]